If your company handles customer data, you may be required to follow cybersecurity rules in India. This means conducting cybersecurity internal audit becomes a necessity.
Understand with us exactly what Indian businesses need to audit, why it’s legally required, and how to get started.
You can also download a full checklist, know frequency guide, and see what a cybersecurity internal audit report covers.
What is a Cybersecurity Internal Audit?
A Cybersecurity Internal Audit is a structured, in-depth review of an organization’s cybersecurity practices, systems, and processes.
It is conducted by your internal IT team, a cybersecurity officer, or a third-party consultant like PKC Management Consulting.
This audit assesses how effectively your organization is protecting its digital assets, data, and infrastructure.
Its key objectives are:
- Identify gaps in cybersecurity defense mechanisms
- Assess compliance with legal and regulatory requirements
- Reduce risks of data breaches, ransomware, and insider threats
- Strengthen operational resilience
- Prepare for external audits such as ISO 27001, CERT-IN, or industry-specific inspections
Legal & Regulatory Compliance in India
In India, cybersecurity is a legal requirement. Failing to comply can lead to penalties, license suspension, lawsuits, or even criminal charges:
Here are the laws that set standards for cybersecurity audits in India:
1. Information Technology Act, 2000 (IT Act)
This foundational digital law that mandates:
- “Reasonable Security Practices and Procedures” for companies handling sensitive personal data
- Liability under Section 43A for data breaches caused by negligence
- Punishment under Section 72A for unauthorized data disclosure
- Section 70B establishes CERT-IN, India’s official cyber emergency response team
2. Digital Personal Data Protection (DPDP) Act, 2023
It governs collection, storage, and processing of personal data. It’s modeled on global standards like GDPR.
Key requirements:
- User consent mechanisms
- Purpose limitation and data minimization
- Data breach notification to individuals and the Data Protection Board (DPB)
- Appointing a Data Protection Officer (DPO) (if applicable)
3. CERT-IN Guidelines (2022)
It enforces strict timelines and practices for incident reporting.
Key mandates:
- Report all cyber incidents within 6 hours
- Store system logs for 180 days
- Applies to: Cloud providers, VPNs, Data Centers, ISPs, and any Indian businesses serving international clients
4. RBI Cybersecurity Framework
Applicable to banks, NBFCs, and fintech firms, it mandates:
- Regular cybersecurity audits
- Cyber Crisis Management Plan (CCMP)
- Risk-based cybersecurity controls
5. SEBI Cybersecurity Regulations
Financial entities such as stockbrokers, exchanges, mutual fund companies must follow SEBI’s cyber resilience framework.
Requirements include:
- Logging cyber incidents
- Maintaining an updated cybersecurity policy
- Annual cybersecurity audits
6. IRDAI, TRAI, and MeitY Guidelines
Sector-specific regulations for:
- Insurance companies (IRDAI)
- Telecom service providers (TRAI)
- Technology and digital infrastructure (MeitY)
7. ISO/IEC 27001 (Voluntary but Highly Recommended)
While not a legal requirement, ISO 27001 is a globally recognized standard for Information Security Management Systems (ISMS).
Many Indian IT, BPO, and data-driven companies adopt it to showcase international compliance.
Who Needs a Cybersecurity Internal Audit in India
If your organization uses the internet, handles data, or operates any digital infrastructure, you need a cybersecurity internal audit, either for compliance or for data protection.
Here are some organisations that must consider cybersecurity audits:
1. RBI-Regulated Entities
RBI mandates comprehensive cybersecurity frameworks, risk-based controls, and annual audits for financial institutions.
These include banks, NBFCs, digital lending platforms and payment operators like wallets and UPI apps.
Audit must assess:
- Cybersecurity risk management
- Business continuity and crisis response
- Network and infrastructure security
2. SEBI Regulated Organisations
SEBI requires all market participants to comply with a Cybersecurity and Cyber Resilience Framework.
These include Stock exchanges, mutual fund houses, asset management companies and capital market intermediaries.
Audit checks:
- Cyber incident reporting
- System backups and restoration
- Policy enforcement and training
- Yearly internal and external audits
3. IT, SaaS & Cloud-Based Companies
These companies manage critical infrastructure for others, often across borders. Clients demand proof of compliance with ISO 27001, SOC 2, or GDPR.
Audit helps verify:
- Secure cloud configurations
- Access control and user management
- Penetration testing and patch management
4. E-Commerce & Online Platforms
They collect payment info, personal data, and operate high-traffic portals, making them major cyber targets.
Internal audits should cover:
- API security and transaction safety
- Data encryption and storage
- Third-party integration risks
5. Healthcare Providers & HealthTech Platforms
Electronic Health Records (EHRs) and medical data are highly sensitive and often targeted by cybercriminals.
Audit ensures:
- Patient data protection
- HIPAA/GDPR alignment (if applicable)
- Medical device network security
6. Large Enterprises with Remote or Hybrid Teams
Distributed teams increase the risk of endpoint vulnerabilities, unsecured connections, and shadow IT.
Cybersecurity audit must assess:
- VPN and endpoint security
- BYOD and device compliance
- Security awareness training
7. Companies Storing Sensitive Personal Data (SPDI)
Under Section 43A of the IT Act, companies handling Sensitive Personal Data or Information (SPDI) are liable for not implementing “reasonable security practices.”
Data includes:
- Aadhaar numbers
- Financial info
- Biometric or health data
- Employee HR data
8. Government Departments & Public Sector Units (PSUs)
CERT-IN mandates internal and external audits for many government bodies to protect national digital infrastructure and citizen data.
Audit verifies:
- Compliance with CERT-IN 2022 directions
- Logging and monitoring of cyber events
- Breach preparedness and reporting
9. Organizations Using Third-Party Vendors for IT, Cloud, or Payroll
Under the DPDP Act, your organization is still responsible even if data breaches occur through third-party processors.
This is specially relevant for Fintech, HR platforms, SaaS, Cloud-based service models, BPOs and KPOs
Internal audit checks:
- Vendor compliance and contracts
- Data sharing and retention policies
- Outsourced infrastructure risks
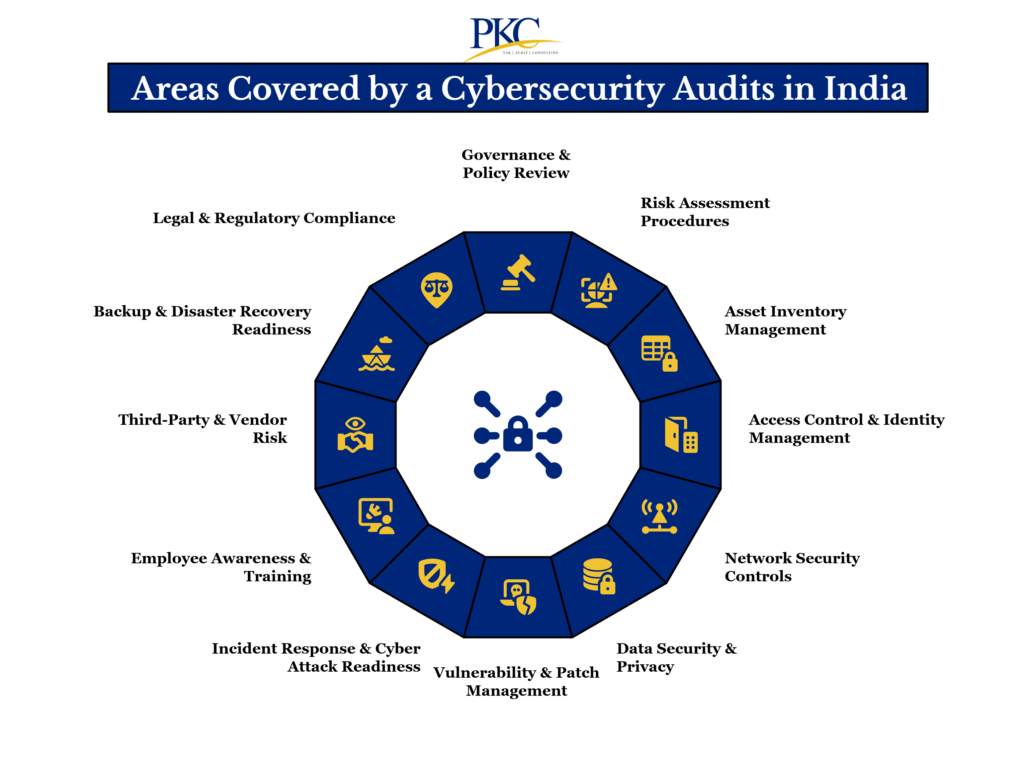
Areas Covered by a Cybersecurity Audits in India
A cybersecurity internal audit evaluates the entire digital ecosystem, and not just antivirus or firewalls.
It’s meant to uncover vulnerabilities, ensure compliance, and help protect sensitive data from growing cyber threats.
Here are the core areas auditors will examine:
1. Governance & Policy Review
- Up-to-date information security policies
- Alignment with ISO 27001, NIST, CERT-IN, DPDPA 2023
- Cyber risk roles, responsibilities, and board oversight
2. Risk Assessment Procedures
- Threat modeling & business impact analysis (BIA)
- Cyber risk register and mitigation planning
- Regular updates based on evolving threat landscape
3. Asset Inventory Management
- Inventory of all IT assets (hardware/software)
- Shadow IT identification (unauthorized apps/devices)
- BYOD risks and device control policies
4. Access Control & Identity Management
- Role-based access control (RBAC)
- Multi-Factor Authentication (MFA) enforcement
- Privileged access & offboarding checks
5. Network Security Controls
- Firewall configurations, IDS/IPS deployment
- Network segmentation for critical systems
- Secure traffic monitoring & logging
6. Data Security & Privacy
- Encryption (data at rest/in transit)
- Consent and data processing practices (DPDPA focus)
- Data minimization, retention, disposal policies
7. Vulnerability & Patch Management
- Routine vulnerability scans
- Patch deployment tracking and SLAs
- Legacy system management
8. Incident Response & Cyber Attack Readiness
- Cyber Incident Response Plan (CIRP)
- Security Information and Event Management (SIEM) tools
- CERT-In reporting within 6 hours of breach
9. Employee Awareness & Training
- Cybersecurity awareness programs
- Phishing simulations and results tracking
- Insider threat education and behavior monitoring
10. Third-Party & Vendor Risk
- Security due diligence for vendors
- Data protection clauses in contracts
- SLA monitoring for compliance
11. Backup & Disaster Recovery Readiness
- Backup frequency and restoration testing
- RTO (Recovery Time Objective) & RPO (Recovery Point Objective)
- Offline and cloud-based backup strategies
12. Legal & Regulatory Compliance
- Adherence to CERT-In Guidelines, DPDPA 2023, IT Act, 2000 (Sec 43A, SPDI Rules), RBI, SEBI, IRDAI, and other sector-specific rules
- Retaining logs for 180 days
- Timely regulatory notifications and reports
Sample Cybersecurity Internal Audit Checklist India
Here is a sample of how a cybersecurity audit checklist should look like. You can tweak it as per your industry, size, and risk profile.
How Can PKC Help With Cybersecurity Audits?
✅ Industry-specific cybersecurity audits: BFSI, healthcare, IT
✅ Cloud computing security audits for modern businesses
✅ End-to-end process audits identifying operational vulnerabilities
✅ Same-day response to critical security audit queries
✅ Dedicated knowledge teams staying ahead of regulations
✅ Business advisory integration strengthening security posture
✅ Multi-location audit capabilities across India operations
✅ Vulnerability scanning and penetration testing
✅ Actionable reports with prioritized risk remediation
How Often Should Indian Companies Do Cybersecurity Audits?
All organizations with digital infrastructure must conduct annual cybersecurity audits as mandated by CERT-In’s 2022/2025 guidelines.
Apart from this sector-specific regulations may require more frequent reviews such as:
- RBI: Quarterly VAPT, semi-annual internal audits (Banks/NBFCs)
- SEBI: Annual/biannual audits, resilience drills
- IRDAI: Annual audits per IT policy
- Healthcare/Telecom: Follow SPDI Rules, CERT-In, and industry norms
Additionally, event-driven audits may become necessary following security incidents, major system changes (like cloud migrations), or the introduction of new regulatory requirements.
Here’s a quick look at audit frequency industry wise:
| Sector / Company Type | Audit Frequency | Regulation / Standard |
| Banks & NBFCs | 6–12 months | RBI, CERT-In |
| Stockbrokers / AMCs | Annually | SEBI Cyber Resilience |
| IT / SaaS Companies | 12 months | ISO 27001, SOC 2, GDPR |
| E-Commerce | Annually | CERT-In, PCI DSS |
| Healthcare Providers | 12 months | SPDI Rules, CERT-In, HIPAA |
| Govt Depts / PSUs | Annually | CERT-In, MeitY |
| SMBs / Startups | 12–18 months | CERT-In (Best Practice) |
| Cloud / Data Centers | Annually | CERT-In, ISO 27001 |
Sample Cybersecurity Internal Audit Report
A cybersecurity internal audit report contains the following:
1. Executive Summary
- Purpose and Scope
- Overall Assessment that highlights critical risks, areas needing improvement, and existing strengths.
- Key Recommendations
2. Audit Details
- Audit ID/Name
- Dates
- Type
- Scope
- References of guidelines, laws or circulars
3. Observations & Recommendations
- Domain
- Key Issues
- Severity
- Actions Needed
Example:
| Domain | Key Issues | Severity | Actions Needed |
| Endpoint Protection | Outdated antivirus on 30% of systems | Medium | Upgrade antivirus and enforce auto-updates |
| User Access Controls | Excessive privileges | High | Enforce least privilege policy |
| Vulnerability Testing | Critical ERP vulnerabilities | Critical | Patch and retest ERP system |
4. Summary of Key Actions Performed
Explains what the auditors looked into and what tools and techniques they followed to assess cybersecurity measures.
Examples:
- Reviewed configurations and logs
- Interviewed key personnel
- Audited compliance documentation
- Tested incident response procedures
5. Incident Summary
- Type
- Impact
- Response
- Prevention
- Status
6. Detailed Recommendations (Prioritized)
Recommendations are prioritized by risk level and focus on system security, policy enforcement, and employee awareness. These actions aim to improve overall cybersecurity posture.
7. Management Response & Remediation Plan
To be completed by management. Includes comments on findings and deadline commitments for corrective actions.
8. Appendices
Includes:
- Technical scan and penetration test results
- Interview records
- CERT-In checklist
- Comparison with past audit findings
FAQs on Cybersecurity Internal Audit
1. What is the role of a cybersecurity audit?
A cybersecurity audit evaluates your organization’s digital defenses to uncover vulnerabilities, threats, and non-compliance issues. It ensures that your data, systems, and networks are protected according to industry standards and Indian cybersecurity regulations.
2. What are the main objectives of an internal cyber security audit?
The goal is to identify security gaps, verify if security controls are working, and reduce cyber risk exposure. It also checks if your business is compliant with frameworks like ISO 27001, CERT-IN, and the IT Act 2000.
3. What does a cybersecurity audit do?
A cybersecurity audit reviews all aspects of your IT environment, network, access controls, data storage, and employee practices. It helps detect weaknesses, improve defenses, and prepare for regulatory compliance or external certifications.
4. What is the difference between IT audit and cybersecurity audit?
An IT audit looks at overall IT operations, including software, hardware, and business processes. A cybersecurity audit focuses specifically on security risks, data protection, and preventing cyber threats.
5. What are the types of cyber security audit?
There are three main types: Internal audit (done by your team), external audit (done by a third party), and compliance audit (to meet standards like ISO 27001, PCI DSS, or RBI rules).
6. What is SIEM in cyber security?
SIEM stands for Security Information and Event Management. It’s a system that collects and analyzes logs from your network in real-time to detect suspicious activity or cyberattacks.

 Expert verified
Expert verified 

